A Comprehensive Guide and Checklist to API Security Testing
In the world of interconnected software, API is the driving force behind all modern applications. From your favorite social media platform to your bank’s mobile application to your online shopping app, all modern digital interactions use APIs.

With the rise in the adoption of virtualization, micro-services, and cloud-native technologies, including cloud engineering services, the interaction between service entities through API has increased. Businesses depend on API to facilitate smoother communication between software systems and services.
Businesses use API to streamline their processes, improve user experience, and drive innovation across diverse industries. Moreover, APIs make it easier to add functionalities and features to applications.
For example, a business can hire the best Salesforce developer to integrate Salesforce API into their CRM system. This can help them customize CRM to their specific needs.
APIs are the hidden backdoors and are vital components of modern applications. But similar to any other door, hackers can easily exploit them if left unprotected. A single breach can expose private user data or other sensitive information. Thus, API security testing is important.
Businesses must hire the best software development company experienced in API integration and development to protect security.
As one of the leading software development companies, TRooTech has been offering end-to-end API integration and development services to businesses across various industries like Travel, Education, Logistics, Healthcare, and Fintech to name a few.
Our extensive expertise and experience in API development and integration have enabled us to cater to varying business requirements like modernizing software solutions, upgrading existing legacy systems to modern cloud architecture through an effective cloud migration strategy, API configuration, API automation, testing APIs, and more.
Our team recently came across a report generated by Cloudflare’s security team that predicts that in 2024, there will be an increased loss of control and complexity and easier AI access, which will lead to higher API risks and business logic-related frauds.
This report was thoroughly reviewed by our senior API expert. Based on the review, a critical concern regarding APIs comes to light: Building a secure API fortress.
Our expert suggests that businesses must understand the importance of testing API security and adopt the right tools and practices to protect their APIs against threats.
It does not matter if you hire the best Azure developers for your API integration services or hire AWS developers with a vast amount of industry expertise. The security of your APIs requires your active involvement and must not be overlooked.
With the help of our seasoned API specialists and subject matter experts, we have created a complete guide to API security testing. This guide uncovers the importance of API security testing and various challenges surrounding API security, helps you identify the best API security testing tools to protect your API from vulnerabilities, and suggests industry best practices to safeguard your APIs.
Let’s dive right in!
Why Do You Need API Security Testing?

As an enterprise or a business owner, maintaining data privacy and safety is a major concern. So, the first reason why you need API security testing is to prevent data breaches by hackers. Here are some other key reasons to protect your APIs.
1. APIs Are Vulnerable and Are Becoming Increasingly Common
APIs are a common component of almost every software application. Every application that is being developed today has at least one call to API, which mostly is controlled by another corporate entity. This means there are increased chances of vulnerabilities and security risks.
Internal teams need to maintain an API security testing checklist to make sure that the application or its sensitive data is not exposed.
2. Increased Use of DevOps and CI/CD Approach Puts APIs at Risk
More businesses adopt a DevOps and CI/CD approach for the development and release of software. Developing a code is now quicker than it was a few years ago. Unfortunately, this also means that a security vulnerability can easily make its way into your code.
By integrating API security testing with the CI/CD approach, businesses can mitigate risks effectively.
3. There Is a Need to Make Sure That an API Is Working as Intended
API security testing and API functionality testing go hand-in-hand. You need to test your API to make sure that it is behaving as required. Ideally, this would be a part of functionality testing. But there are some cases where it is also an important element of security testing.
For example, suppose you want to integrate an Amazon AWS API into your healthcare application. For that, you need to avail of AWS consulting services for Healthcare. To do so, you will need to hire AWS developers who can integrate the API successfully into your application.
Once the API has been integrated, the development team will need to test whether or not the API is returning the data correctly. This is a part of functional testing, but it is equally relevant to security.
According to Zipdo, the API gateway market size in 2024 will be around USD 1.6 billion – thanks to the increasing API diversity. As we move toward a Low-Code No-Code development, growing API gateways and integration, and microservices architecture, the need to protect API security is urgent.
Let us briefly review the threats that are likely to expose your API to threats.
However, without understanding API risks and attacks, it is impossible to choose the right API security testing tools to mitigate those risks.
Build User Trust and Ensure Compliance
We Perform Automated Vulnerability Scanning to Identify and Prioritize Threats
Top API Threats and How to Prevent Them
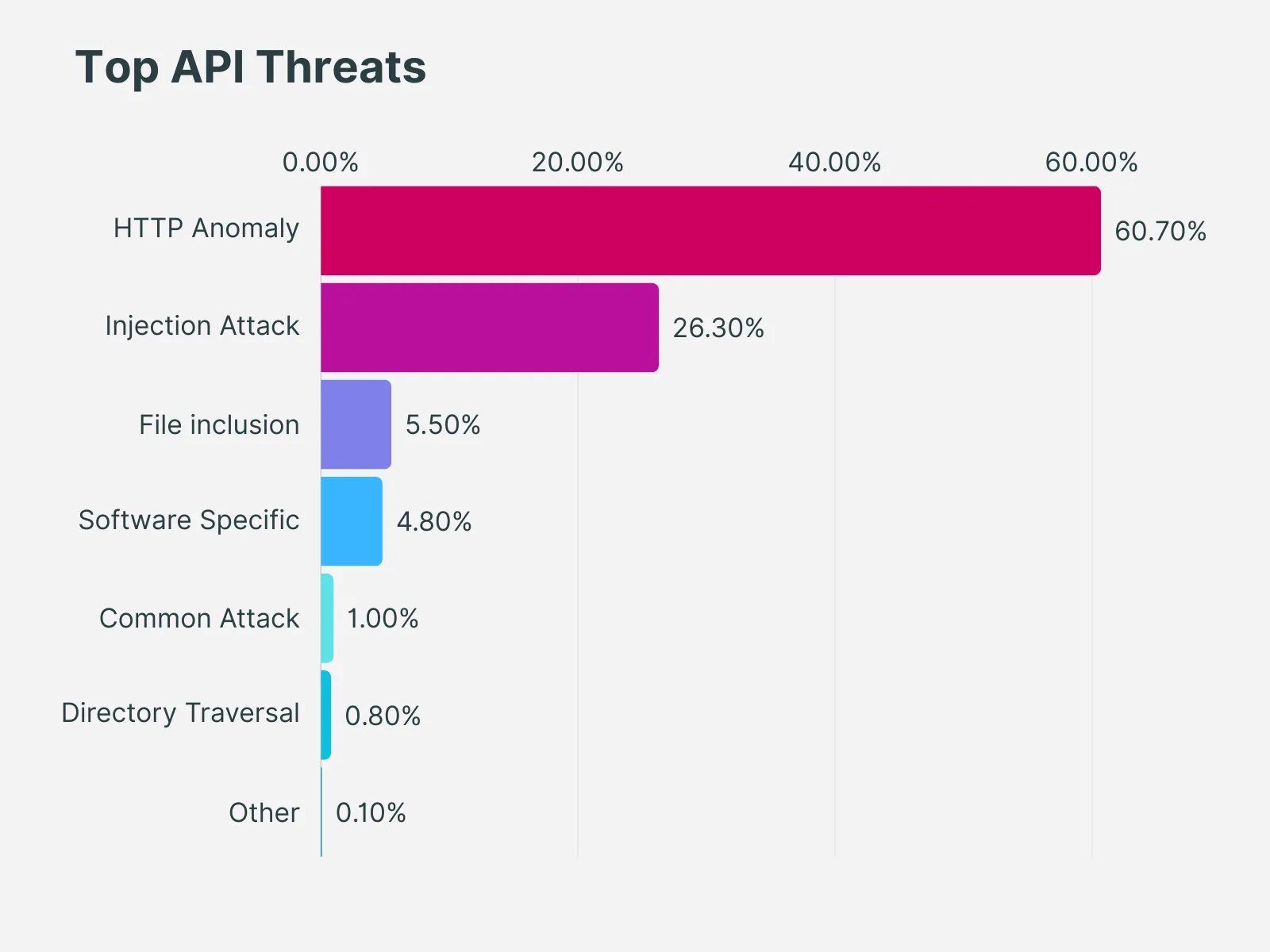
Additionally, OWASP has released an API Security Top 10 list in 2023, highlighting the top API security threats that are likely to expose your organization’s data to hackers or malicious attackers.
Based on both these reports and assistance from our technical experts, we have created a list of the top 10 API threats and how you can prevent them.
1. Broken Object-Level Authorization
It is the most common API security threat. Due to a lack of proper access controls on API endpoints, unauthorized users can access and modify sensitive data. About 40% of API attacks are represented by Broken Object-Level Authorization.
Steps to Prevent This
- Implement a mechanism for authorization that relies on user policy and hierarchy.
- Using this mechanism, check if the user who is logged in has access to perform the requested action on the record.
- Use random or unpredictable values as GUIDs for the ID of the records.
- Create tests that can evaluate how vulnerable an authorization mechanism is. Avoid making changes that are likely to result in test failure.
2. Broken Authentication
This API security threat allows attackers to gain unauthorized app access through stolen tokens, credential stuffing, and brute-force attacks.
Steps to Prevent This
- Ensure that you are aware of all possible flows related to API authentication. Consult your engineering team to make sure you have not missed any flow.
- Keep yourself updated with the authentication mechanism. Try to get an idea about how they are used.
- Avoid reinventing the wheels in authentication, token generation, and password storage. Only use the standards.
- Endpoints like credential recovery, forgot password, etc. should be treated as login endpoints in case of brute force, rate limiting, and lockout protections.
- Implement re-authentication for operations like changing the email address of the account owner, and contact details, and other such sensitive operations. Also, implement multi-factor wherever you can.
- To reduce occurrences of credential stuffing, dictionary attacks, and brute force attacks on your authentication endpoints, implement anti-bruce mechanisms. Make sure that this mechanism is stricter than other similar rate-limiting mechanisms.
- Perform mechanisms like account lockout and captcha to prevent hackers from carrying out brute force attacks against specific users. Implement checks to filter out weak passwords.
- Avoid using API keys for user authentication. Instead, only use them for API client authentication.
3. Broken Object Property Level Authorization
This threat occurs when an attacker can access or modify specific properties of another user's data, even without having access to the entire object.
Steps to Prevent This
- Whenever you expose an object through an API endpoint, you must ascertain that the user has access to those properties of the object that you choose to expose.
- Refrain from utilizing generic methods like _json() and to_string(). In place of that, select a specific object property that you want to return.
- It is preferable if you avoid using functions that are likely to bind a client’s input into code variables, internal objects, or object properties automatically.
- Enable changes to the object’s properties that the client should update.
- Enforce a schema-based response validation mechanism to add an extra layer of security. Define and enforce data that is returned by all API methods as a component of this mechanism.
- Make sure that you keep returned data structures to a bare minimum, in line with the business and functional requirements of the API endpoint.
4. Unrestricted Resource Consumption
This API threat occurs in APIs that have not implemented reasonable or proper limits on resource consumption. As a result, the APIs become vulnerable to susceptible or brute-force attacks.
Steps to Prevent This
- Businesses can implement a solution that makes it easier for them to limit memory, CPU, restart frequency, and file descriptors. We would advise you to use a serverless code like Lambdas.
- For all incoming parameters and payloads, businesses must define and enforce a maximum data size. This includes the maximum length for strings, the maximum elements in an array, and the maximum size of the file.
- You must set a limit on the frequency with which a client can interact with an API in a certain timeframe, also known as rate limiting.
- Additionally, ensure that rate limiting is fine-tuned to specific business needs. The reason behind doing so is that some API endpoints might require stricter policies.
- Businesses must place a limit on how many times a specific API client or user can carry out a single operation; i.e., how often they can request password recovery, validate an OTP, etc.
- You must add a proper server-side validation for query string and request body parameters.
- It is ideal to set a configuration limit on spending for all service providers and API integrations. If it is not possible to set a spending limit, then you must configure billing alerts.
5. Broken Function Level Authorization
This API threat is likely to occur when there is a flaw in authorization due to complex access control policies within various hierarchies, groups, and roles. It can also occur due to an unclear separation between administrative and regular functions.
Attackers can easily exploit these issues and gain access to the resources of other users and administrative functions.
Steps to Prevent This
- Your application must have an authorization module that is not only easy to analyze but also consistent.
- Enforcement mechanisms must deny default access and instead, require grants for specific roles to provide access to every function.
- You must review your API endpoints against function-level authorization flaws. At the same time, it is important to note the application’s business logic and hierarchy of the groups.
- You must make sure that all your administrative controllers are based on an abstract controller that checks and grants access to users based on their group and role.
6. Unrestricted Access to Sensitive Business Flows
APIs that are vulnerable to this threat can lead to the risk of exposing a business flow such as posting a comment, buying a ticket, etc. If the API is continually used in an automated manner, it poses a threat to business functionality.
Steps to Prevent This
- A thorough mitigation planning must be done at a business level and an engineering level.
- Use device fingerprinting to deny service to unexpected client devices.
- Implement human detection techniques through advanced biometric technology and solutions like Captcha.
- Regularly analyze user flow to detect non-human patterns in it.
- Block the IP address of Tor exit nodes as well as other well-known proxies.
7. Server-Side Request Forgery
This particular flaw occurs when the API fetches a remote source without validating the URL supplied by the user first. This allows the hacker or attacker to manipulate the application into sending a crafted request to an unexpected destination. This may take place even when the application is protected by a firewall or a VPN.
Steps to Prevent This
- You must isolate the resource-fetching mechanism within your network.
- Use allow lists ‘remote origins’, URL schemes, and ‘media type’ whenever possible.
- Disable HTTP redirections
- Implement and use a well-tested and maintained URL parsing mechanism to prevent issues related to inconsistent URL parsing.
- Validate all input data supplied by the client.
8. Security Misconfiguration
APIs as well as the systems that support APIs have complex configurations. These are necessary to make APIs more customizable. However, even if you hire the top DevOps developers or software engineers, they might miss these configurations or fail to follow the API security testing checklist and best practices.
Steps to Prevent This
- A hardening process that provides quick and easy deployment of a properly locked down environment.
- Task review and update for configuration for the entire API stack. This should include orchestration files, API components, and cloud services.
- An automated process that can assess the configuration’s effectiveness continuously as well as the effectiveness of the settings in all environments.
- Implement encrypted communication channels for all API communication taking place between the client and the API server.
- Specify which HTTP verbs each API can access. Disable all other HTTP verbs.
- Ensure that all servers that are in the HTTP server chain such as load balancers, reverse and forward proxies, back-end servers, etc. process all incoming requests in a uniform manner. This helps in avoiding issues related to desync.
- All APIs that are designed to be accessed through browser-based clients must implement a proper Cross-Origin resource-sharing policy. Moreover, they should include relevant and applicable security headers and restrict incoming content types and data formats to ensure they meet business and functional requirements.
- You must define and enforce all API response-related payload schemas wherever applicable. This includes error responses and other such information.
9. Improper Inventory Management
Sometimes APIs tend to expose more endpoints compared to traditional web applications. Thus, it is important to maintain proper documentation and update it properly. It is also critical to maintain a proper inventory of hosts and API versions that have been deployed.
Steps to Prevent This
- Make an inventory of all API hosts and document important aspects of each API host. Ensure that the aspects focus on the API environment like production, staging, testing, and development, and who gets access to the host.
- Inventory integrated services and document important aspects of each one of them. This includes their role in the system, which data is exchanged, and its sensitivity.
- Document all aspects of your API. This includes authentication, errors, redirects, rate limiting, cross-origin resource sharing policy, and endpoints, which include their parameters, requests, and responses.
- Adopt open standards to automatically generate documentation. See to it that this documentation is also built into your CI/CD pipeline.
- Create API documentation that can be accessed by only those people who are authorized to use the API.
- For exposed versions of your API, you must use external protection measures that are specific to API security.
- It is advisable to not use production data with non-production API deployments.
- If the new versions of API require security upgrades or improvements, perform a risk analysis.
10. Unsafe Consumption of APIs
Sometimes, developers are likely to trust the data received from third-party APIs more than that provided by user input. This leads to the implementation of weaker security standards. As a result, hackers and attackers attack the integrated third-party services instead of directly attacking the target APIs.
Steps to Prevent This
- Assess the security posture of the APIs when you evaluate a service provider.
- Make sure that all API interactions take place over a secure communication channel.
- Validate and sanitize all data received from integrated APIs before you use it.
- Create and maintain an allowed list of well-known locations wherever the integrated APIs may redirect to yours. Do not simply follow redirects without checking first.
Fortify Your API Infrastructure and Elevate Its Security
We Help You Implement Cutting-Edge Solutions to Make Your Digital Ecosystems Resilient
How to Maintain an API Security Testing Checklist

Maintaining a testing checklist helps businesses identify security threats at an early stage. Our experts suggest the following ways to ensure step-by-step security of your APIs.
1. Authenticate and Authorize APIs
To control access to API resources, it is necessary to properly identify all users and devices related to it. To do so, use standards like OAuth 2.0, OpenID Connect, and JSON web tokens to authenticate API traffic and define access control rules and grant types.
2. Use Access Control
Introduce and test controls to manage third-party access determining when, how, and who can get access to internal data and systems through APIs.
Our experts advise keeping APIs behind a firewall, web application firewall, or an API gateway that can only be accessed through a secure protocol such as HTTPS. This will offer baseline protection to APIs.
3. Encrypt Requests and Responses
Encrypt all network traffic, especially API requests and responses, since they are likely to contain sensitive data. Enable HTTP Strict Transport Security wherever possible. Ensure that all APIs use and require HTTPS.
For instance, TRooTech’s Microsoft Dynamics 365 developers use protocols like HTTPS/TTLS to encrypt data that is transmitted among clients and Dynamics 365 APIs to prevent it from being tampered with.
4. Clean and Validate your Data
Do not assume that the API data you receive has been cleaned or validated correctly. You must implement your own data cleaning and validation practice to prevent injection flaws and cross-site request forgery attacks.
Use debugging tools like Postman and Chrome DevTools to examine the APIs' data flow, track errors, and trace anomalies.
5. Conduct API risk assessment
Perform a risk assessment of all APIs that are in your existing registry. Enforce measures that assure that the APIs meet security policies and are not vulnerable to risks.
This helps in identifying systems and data that are affected due to compromised APIs. It also helps you devise an appropriate API strategy to mitigate risks.
An important thing to ensure here is that you document the review dates and repeat assessments whenever a new threat arises or when you modify the API.
6. Only Share Necessary Information
API responses generally include the record of the entire data instead of the relevant fields. They rely on the client-side application to filter out what the user sees. Besides slowing response times, it also gives attackers access to additional information related to API.
Ensure that the responses must contain only the minimum information that is necessary to fulfill a request.
7. Maintain an API Registry
You can’t secure something if you don’t know what you’re securing. Record all APIs in a registry to define their characteristics like name, purpose, usage, access, live date, retired date, and owner. This will help detect and eliminate shadow and silo APIs.
To ensure that you meet the audit and compliance requirements, record the details of the information that you log. Proper documentation is important for third-party developers who want to integrate the APIs into their projects.
The API registry you maintain must have links to the document and manuals that contain information on technical API requirements.
8. Conduct Routine API Security Checks
In today’s cloud-driven world, it is necessary to secure your APIs. Both Microsoft Azure and Amazon AWS offer robust security solutions. To guide you in choosing the right service for your business needs, you can refer our comparative guide on Azure vs AWS.
Besides testing APIs at a developmental stage, it is necessary to keep testing them to make sure that they are functioning as expected and performing as documented.
Your security teams must regularly check security controls to protect live APIs. This can be done through routine checks by using appropriate API security testing tools.
At the same time, incident response teams must also create a plan to handle alerts that are produced by threat detection and other security controls that suggest an API attack.
If you wondering how to test API security, don’t worry. We have identified some of the best API security testing tools for securing your APIs.
Uncover Hidden Vulnerabilities Within Your APIs Before They’re Exploited
Stop Hackers in Their Tracks Through Comprehensive API Security Testing
Top API Security Testing Tools

1. Postman
It is a multifunctional API security testing and development tool. It offers capabilities such as API security assessments. It has a user-friendly interface that allows the developers to create, send, and manage HTP requests.
Further, Postman also offers features like request automation and scripting which support comprehensive API testing.
Features
- It can be used for automation and automating the scripting of test cases.
- Users can access and utilize dynamic variables to run diverse data scenarios and test app codes.
- Postman supports the management of testing environments and variables. Using this feature, users can easily customize and adapt to different configurations.
- It has an interactive user interface and versatile features that help testers locate API vulnerabilities easily.
2. Assertible
Assertible is a web-based API tool. It is designed for continuous integration and deployment. The tool has several features including automated testing, monitoring, and API and web service validation.
The tool is simple and easy to use because of its components like scheduled testing, in-depth assertions, and seamless integrations with popular CI/CD tools. The tool also offers features like real-time alerts and comprehensive reporting.
Features
- It performed automated API testing and monitoring.
- Assertible supports easy test creation for RESTful APIs, web services, and websites. It also provides support for diverse HTTP methods and authentication types.
- The tool provides flexible assertion definitions as well as JSON and XML validation, and environment variable support for dynamic tests.
- It offers a user-friendly interface and robust integration with CI/CD tools.
- It also provides comprehensive test monitoring features.
3. Apidog
This tool is a versatile API documentation and testing tool. It enables organizations to streamline the creation and maintenance of API documentation. Developers can use this tool to automatically generate documentation using code comments.
This helps them ensure that the API documentation is up-to-date with the codebase. With Apidog, development teams can easily share and collaborate on API documentation.
Features
- Apidog is a master tool for API development and debugging. It also helps in tracking API documentation and in automated API testing.
- It offers an automated testing suite that works seamlessly in the testing environment. Additionally, it also checks for vulnerabilities.
- The API automated testing suite of Apidog works seamlessly with the testing environment and checks for all kinds of vulnerabilities.
4. SoapUI
SoapUI is among the leading API testing tools that have been created to simplify the testing of web services. It provides support for both SOAP and RESTful APIs. Moreover, it also provides a user-friendly interface that can be used to create, execute, and automate test cases.
The tool facilitates functional, security, and performance testing which makes it an all-in-one solution for API quality assurance.
Features
- It is a versatile tool for API testing that provides support for the testing of SOAP and RESTful web services.
- It is built with an intuitive interface and can be used to design and execute several API test cases.
- It supports request and response inspection, which ensures the integrity of the API code.
- The SoapUI offers a user-friendly interface that supports performance and regression testing and easy integration with CI/CD pipelines.
- The API tool further offers scripting support.
4. Katalon Studio
Katalon Studio is an all-in-one platform for automated testing for low-code web, API, Mobile, and Desktop. It offers comprehensive solutions that provide support for various types of testing approaches such as record-and-playback, keyword-driven testing, and more.
Features
- It simplifies the testing process for developers and testers due to its automation-powered API development.
- The tool offers recording and playback functionality through which the developers can test and view testing process results after recording to gather insights.
- The Katalon platform also offers in-built templates which can be integrated into the test environment. This makes it easy to create and maintain test cases and boosts the testing team’s productivity.
Concerned About Ensuring the Integrity of Data Within Your API?
We Help You Adopt a Proactive Approach to Safeguard Your Critical Data With Robust API Security Testing Tools
Secure Your APIs With TRooTech
APIs act as critical gateways to your organization's data and systems. Yet, these powerful connectors often remain inadequately secured, leaving them vulnerable to exploitation.
To deliver secure applications, securing your API is paramount. Organizations need to implement an API-first approach by defining solid parameters on how to test API security and using the best API security testing tools. Not only that, they need to collaborate with experts to proactively identify API threats and secure them against risks and vulnerabilities.
At TRooTech, we work collaboratively with you to develop and integrate custom and third-party APIs for your software, web apps, and mobile applications. Our API integration process is smooth and cost-effective, helping you save development time and costs.
FAQs
API security testing is the process of evaluating the security vulnerabilities and weaknesses within an API (Application Programming Interface) to ensure that it is robust and protected against potential threats. It involves conducting various tests and assessments to identify and address security risks, such as unauthorized access, data breaches, injection attacks, and denial of service (DoS) attacks.
The API security process involves several steps to ensure the protection and integrity of an API. This process typically includes:
- Identifying security requirements and risks associated with the API.
- Implementing security measures such as authentication, authorization, encryption, and validation.
- Conducting security testing, including vulnerability scanning, penetration testing, and code review.
- Monitoring and continuously updating security controls to adapt to emerging threats and vulnerabilities.
API testing is crucial for ensuring the reliability, performance, and security of software applications that rely on APIs for communication and data exchange. It helps identify defects, errors, and vulnerabilities early in the development lifecycle, thereby reducing the risk of security breaches, data leaks, and system failures. Additionally, API testing helps validate the functionality and interoperability of APIs, ensuring seamless integration with other systems and applications.
The cost of API security testing can vary depending on factors such as the complexity of the API, the scope of testing required, the number of endpoints to be tested, and the chosen testing approach (automated vs. manual). Generally, API security testing costs can range from a few thousand to tens of thousands of dollars, but investing in comprehensive security testing is essential to safeguard sensitive data and protect against potential threats.
Several popular tools for API security testing include:
- OWASP ZAP: An open-source web application security scanner.
- Burp Suite: A comprehensive platform for security testing.
- Postman: A versatile API development and testing tool.
- Nessus: A vulnerability scanning tool.
Choosing the right tool depends on your project's requirements, team expertise, and budget.

